Part
01
of one
Part
01
Networking and Networking as a Service Research
Key Takeaways
- Cellular Vehicle-to-Everything (C-V2X) technology is one of the latest innovations in the networking and connectivity space. The technology is "gaining significant traction and momentum with automotive OEMs, electronic module/chip suppliers, and roadside and city infrastructure manufacturers" because they play an instrumental role in helping vehicles become increasingly autonomous.
- Brian Beutler, CEO at Alianza, found that the federally-mandated retirement of plain old telephone service (POTS) lines is one of the main challenges facing the networking and connectivity industry currently.
- One of the key future expected challenges for Networking-as-a-Service (NaaS) will be enabling support for a solid, integrated security system, according to Neil Anderson, senior director, network solutions, at World Wide Technology.
Introduction
An overview of current trends in the networking space, themes for the future of networking, current and future challenges in the networking space, and networking and connectivity innovations has been presented below.
Trends in the Networking Space
- Artificial Intelligence (AI) is among the hottest trends in the networking industry. Remote work is becoming mainstream and the new challenge is to support users in their individual homes, which is why networking companies are gradually switching to AI solutions that are well suited for the rising remote workforce.
- Some applications of AI solutions for enterprise businesses include a) Cybersecurity — with concerns around cybersecurity of the 5G network, AI solutions in this area are becoming increasingly important; b) Task Automation — many automation solutions that are AI-driven, such as robotic process automation (RPA) tools, are on the rise. Business efficiency is one of the main perks of AI-driven task automation; and c) Virtual Assistants — another practical tool that helps businesses save time and money, often used by sales and customer service teams.
- “SD-WAN is a software-based approach to manage Wide Area networks (WANs).” A recent study has shown that SD-WAN adoption is on the rise. In 2020 alone, the installation of SD-WAN rose from 18% in 2018 to 43%. The main reason behind this SD-WAN boom is the rise of remote working culture. Some of the main benefits of this trend include reduction of operational costs, increased efficiency, data security and privacy.
- Another top industry trend is 5G technology. This trend is still in its infancy phase, but according to TeleGeography data “5G went from constituting 0.4% of global wireless offerings in 2018 to almost 5% in 2021.” Enterprises are slowly shifting their operations to 5G, which is praised for reducing latency, increasing speed and improving flexibility in wireless services. Also, 5G comes with the promise of faster and more flexible connectivity among many IoT devices. However, these new opportunities also bring on new challenges. For 5G, novel cybersecurity concerns are particularly relevant.
Themes for the Future of Networking
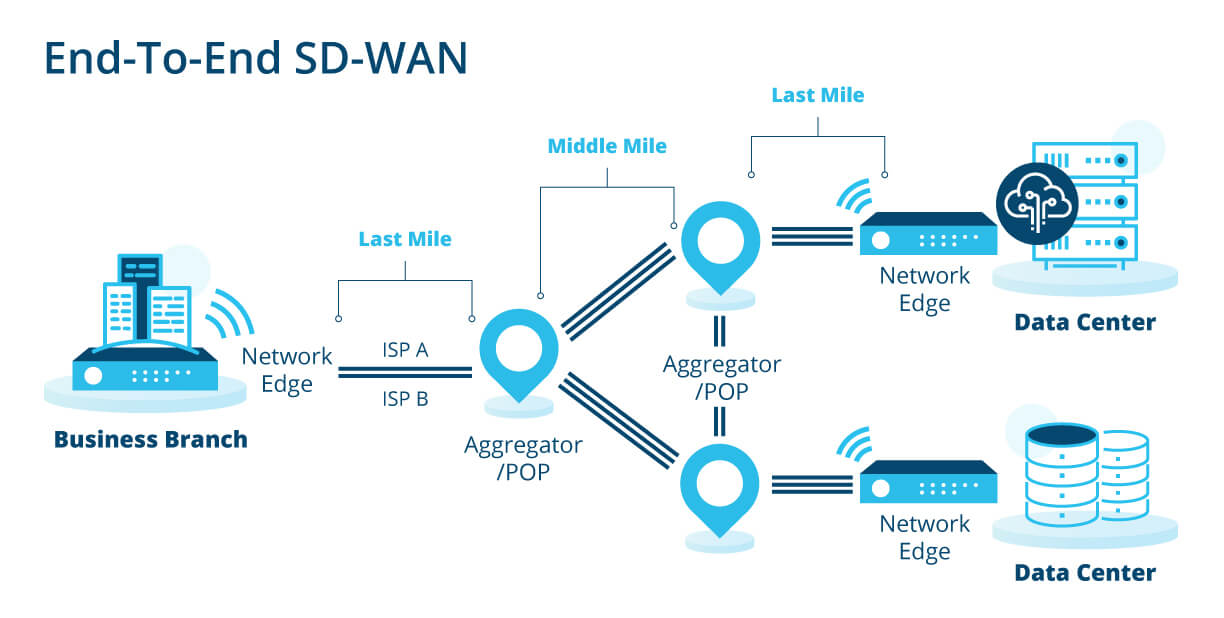
- One of the main themes in the future of networking is the application of End-to-End SD-WAN technology. This theme is primarily driven by the rise of wide area networking. Wide area networking is becoming increasingly popular as businesses continue to evolve into cloud-first and cloud-native deployments.
- Limited vendor options will continue to be one of the main themes in the future of networking, but the way service providers will tackle this issue will differ. As more and more businesses realize that proprietary monolithic networking platforms are restricting their ability to efficiently and cost-effectively grow their network, they are preparing adequate responses, according to Yesmean Luk, Telco Cloud Practice Lead at STL Partners.
- "The value of networks has shifted from the networks themselves to the services that run over them," Luk said. "We are seeing that through the incredible business growth of cloud providers and the huge breadth of cloud-based services and applications that are being rolled out. As operators evolve to more advanced data-intensive connectivity services such as 5G and fiber to the home, they will benefit from the growing demand for capacity and throughput but as their capabilities grow, they will need to manage costs in a more sustainable and optimal way. A cloud-like architecture has been proven to support that and enable new revenue streams from expanded service offerings and the agility to address these. Hyperscale providers serve as the model."
- Disaggregation is also increasingly relevant as service providers realize how it can simplify overall network operations, enabling simplified service innovation and more flexibility. Tom Nolle, President and Chief Strategist at the CIMI Corp, stated that "The virtualization-centric notion of disaggregation and re-aggregation offers an opportunity to build network node functionality and network management visibility almost orthogonally. What the network does and what it looks like don’t have to be congruent. That’s a highly useful concept when it comes to both service features and service lifecycle automation."
- Shin Umeda, vice president of the Dell’Oro Group, reiterated this statement by saying “Our latest forecasts for disaggregated routers reflect CSP’s expanding interest in this rapidly emerging market. We expect disaggregated routers in which the network operating system (NOS) software is sold independently from white box hardware to see their first large-scale deployments in 2021, for use in both high-capacity core networks and as cell site devices in mobile backhaul networks.”
Current Challenges in the Networking Space
- Uptime Institute, a data center resiliency think tank, found that networking issues will soon overtake power supply problems as the most common source of data center outages. Networking-related outages are becoming more frequent due to the “broad shift in recent years from siloed IT services running in dedicated, specialized equipment” to a model where IT systems are distributed and replicated across multiple sites linked together by network connections.
- "Networking issues are now emerging as one of the more common — if not the most common — causes of downtime. The reasons are clear enough: modern applications and data are spread across and between datacentres, with networking ever-more critical"
- Brian Beutler, CEO at Alianza, found that the federally-mandated retirement of plain old telephone service (POTS) lines is one of the main challenges facing the networking and connectivity industry currently. The US Federal Communications Commission (FCC) announced plans to retire these lines back in 2017, placing service providers in "the difficult position of either significantly increasing prices to maintain their legacy copper POTS lines or finding an alternative solution".
Future Challenges in the Networking Space
- One of the key future expected challenges for Networking-as-a-Service (NaaS) will be enabling support for a solid, integrated security system, according to Neil Anderson, senior director, network solutions, at World Wide Technology. With NaaS, a certain amount of security control will lie with the NaaS provider, which can be a big issue, Anderson said. "How will the customer still be able to do traffic inspection, or be able to feed security analytics tools with NetFlow, etc.? And who is liable for a breach and how will it be remediated?"
- Another challenge that businesses will face as NaaS technology becomes more widely adopted are interruptions in connectivity. "Because NaaS is enabled by fast, low-latency, internet services, any interruption in WAN connectivity may seriously degrade or disable enterprise network operations. Because the service is relatively new, NaaS pricing is still uncertain, so business leaders may find that per-year operational costs may be more than they budgeted for," according to Lee Doyle of Network World.
Networking And Connectivity Innovations
- Cellular Vehicle-to-Everything (C-V2X) technology is one of the latest innovations in the networking and connectivity space. The technology is "gaining significant traction and momentum with automotive OEMs, electronic module/chip suppliers, and roadside and city infrastructure manufacturers" because they play an instrumental role in helping vehicles become increasingly autonomous.
- The C-V2X technology is based on LTE (Long-Term Evolution) wireless broadband networks and it enables vehicles to communicate with each other, as well as to city infrastructure and cloud services. This means that it has the potential to enable use cases like "safety and traffic efficiency that encompasses collision avoidance, hazard or road construction warnings, platooning and cooperative driving, as well as other use cases such as toll collection and fuel charge automation."
- Smart trailer technology is another connectivity solution that is expected to rise in popularity. Smart trailers unify data from multiple sensors and telematics devices installed on trailers, providing real-time visibility into each trailer’s location, health, and cargo. These connected trailers allow fleet operators to maximize trailer utilization, a feature that very important due to supply chain disruptions brought on by the pandemic that are expected to continue in the near future.
- While not entirely a new innovation, edge computing is expected to rapidly increase in popularity in the coming years. In fact, experts predict that 75% of all data processing will occur at the edge by 2025. As connected devices continue to get smarter, more and more critical applications are placed at the edge, while Smart Out-of-Band solutions allow businesses to manage infrastructure at remote sites, while maintaining the critical features of resilience, scalability and connectivity that data centers are currently known for.
- Patent 1 — Rolling back kubernetes applications — "A new snapshot of a storage volume is created by instructing computing nodes to suppress write requests. An orchestration layer implements a multi-role application that is provisioned with virtualized storage and computation resources. A snapshot of the application may be created and used to rollback or clone the application. Clones snapshots of storage volumes may be thin clones. An application may use multiple orchestration approaches and objects of the multi-role application may be discovered and added to an application definition. The application definition may be used to create snapshots of the application and perform operations using the snapshots."
- Patent 2 — Health monitoring of automatically deployed and managed network pipelines — "Deployment of a network service pipeline may be automated by defining workflows comprising functions of instances of elements. Workflows may be defined in a graphical user interface including menus for the selection of elements, functions, and predefined workflows. A workflow may be dynamic such that addition or modification of a function invokes a trigger that automatically populates or modifies parameters of the functions of the workflow."
- Patent 3 — Implementing secure communication in a distributed computing system — "A new snapshot of a storage volume is created by instructing computing nodes to suppress write requests. Once pending write requests from the computing nodes are completed, storage nodes create a new snapshot for the storage volume by allocating a new segment to the new snapshot and finalizes and performs garbage collection with respect to segments allocated to the previous snapshot. Subsequent write requests to the storage volume are then performed on the segments allocated to the new snapshot. An orchestration layer implements a multi-role application that is provisioned with virtualized storage and computation resources. A snapshot of the application may be created and used to rollback or clone the application."
- Patent 4 — Embedded Universal Integrated Circuit Card Supporting Two-Factor Authentication — "Network-1 Technologies, Inc. (NYSE AMERICAN:NTIP), a company engaged in the development, licensing and protection of intellectual property, announced today that the European Patent Office issued a Decision to Grant European Patent No. EP3111689 (Embedded Universal Integrated Circuit Card Supporting Two-Factor Authentication), which is being published today in the European Patent Bulletin of July 14, 2021. In addition, the UK Intellectual Property Office issued Intention to Grant letters for Applications GB1608573.0 and GB2100530.1 (both entitled Set of Servers for "Machine-to-Machine" Communications Using Public Key Infrastructure). The UK applications are expected to be granted shortly after July 9, 2021 and August 9, 2021, respectively. The claims in these granted foreign applications are generally directed towards authentication of a module including an embedded universal integrated circuit card (eUICC) with a mobile network and supporting secure communication between the module and the mobile network."
- Patent 5 — Implementing clone snapshots in a distributed storage system — "A new snapshot of a storage volume is created by instructing computing nodes to suppress write requests. Once pending write requests from the computing nodes are completed, storage nodes create a new snapshot for the storage volume by allocating a new segment to the new snapshot and finalizes and performs garbage collection with respect to segments allocated to the previous snapshot. Subsequent write requests to the storage volume are then performed on the segments allocated to the new snapshot."
- Patent 6 — Block map cache — "A new snapshot of a storage volume is created by suppressing write requests. Once pending write requests from the computing nodes are completed, storage nodes create a new snapshot for the storage volume by allocating a new segment to the new snapshot. Subsequent write requests to the storage volume are then performed on the segments allocated to the new snapshot. A block map records segments where current data for an LBA of a slice of a storage volume is stored. Block maps may be written to a storage device in order to free memory. Block maps may be read back into memory when needed. Writing and reading of block maps may be performed upon fragments of block maps. On restarting of the storage node, block maps may be restored from block maps stored in the storage device."
Research Strategy
The research team focused on varied industry expert opinions gathered from multiple industry sources to compile the majority of the research report. The relevant patents have been identified by scouring through the Justia patent database for relevant patents.